
The english term hash (derived from French: hacher), in the information technology industry and specially in electronic signature applications, is related to a short-length alphanumeric string created from a document, sort of its digital fingerprint.
If you are interested in knowing more about hash properties and its major role in both the process of electronic signing and document integrity validation, just keep reading this post.
Fundamental properties of hash functions
A hash function consists in a mathematical algorithm which generates an output alphanumeric string from any document used as input. In general, its applicable to any type of digital file such as documents, images, audios, videos, programs, folders, etc.
Hash functions are one-way. This means, computationally speaking, that is possible and relatively easy to calculate this string but it is not possible to apply an inverse computation capable of generating back the original document from its fingerprint.
Another main property of hash functions is the uniqueness of the calculated string. This property states that any variation on the input document or file, regardless of how minimal it is, will result in a totally different fingerprint.
In the example below, we see a unique alphanumeric string (hash) that corresponds to the digital file
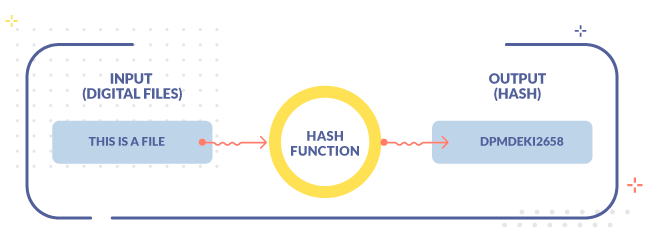
If the file is altered in the slightest, the alphanumeric string would be completely different from the initial one.
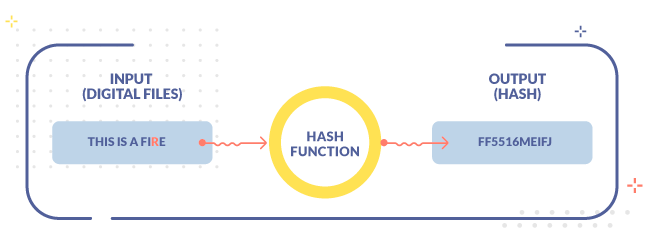
On the other hand, there is no chance of generating two identical fingerprints, this would happen only if the input documents or files are identical as well. This is known as determinism and in case this property is not satisfied, a collision would occur.
Role of hash algorithm in the electronic signature process
The Secure Hash Algorithm (SHA) includes what is considered these days one of the safest family of cryptographic functions. There is special interest on the SHA-256 algorithm, which besides being part of the technology that made possible the development of Bitcoin, is also widely extended in applications related to electronic signature.
There are also algorithms that generate longer hash strings like SHA-384 or SHA-512, but those strings require greater bandwidth to be transported as well as greater calculation memory space and processing capacity, whereas the gain in security does not represent a significant increase compared to SHA-256. Moreover, exists a risk of experiencing compatibility problems when they are implemented on systems not able to recognize them.
To produce an electronic signature, the SHA-256 generated must go through an asymmetric encryption process. The RSA (from Rivest, Shamir and Adleman, their creators in 1979) algorithm performs this action. It works with two cryptographic keys: a private key, always possessed by the signer and a private key, available for any recipient of the document that is sent.
The process starts when the hash string is generated and encrypted at the time the sender applies the signature by means of his or her private key, then the encryption result is attached to the document, along with the signer’s digital certificate which contains the public key. This public key is hugely important because it makes possible the forthcoming verification process.
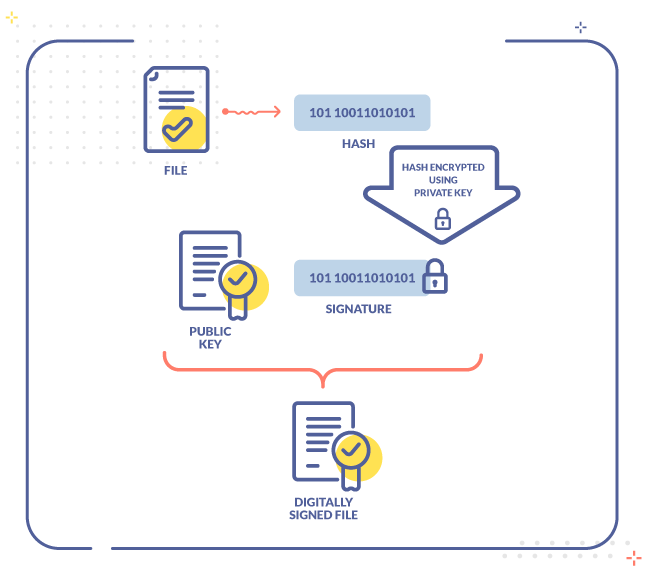
In case of a PDF-format signed document, both the encrypted hash (formally understood as the signature) and the digital certificate are inserted into a specific PDF’s data structure, technically known as “signature dictionary”. This structure may contain optional information, e.g. a timestamp. This adequation of the signature to a PDF-format document in compliance to ISO 32000-1 is defined as PAdES.
Hash: key factor of the signature validation process
When a recipient validates an electronically signed document, at an application level an automatic process involving two main actions occurs: first, the generation of a new hash string from the original document. Second, the decryption of the hash stored in the mentioned document structure. This is performed by means of the public key present in the digital certificate which, as said before, is also included in the document.
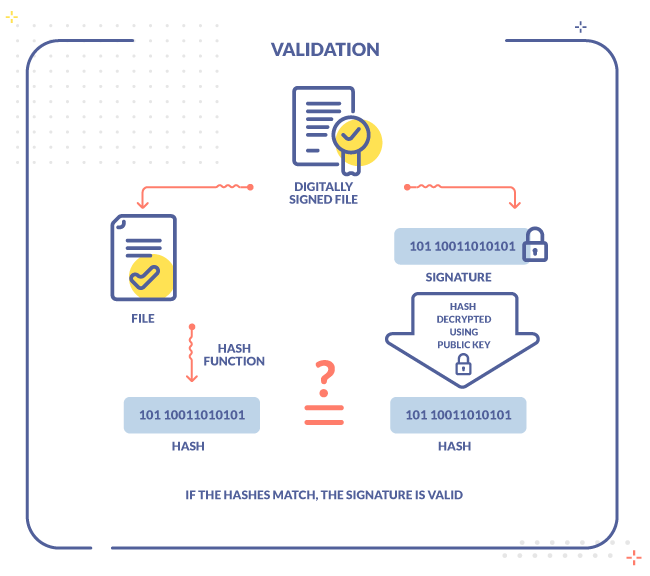
Because the signed hash has a unique and direct connection to the document it represents, only by generating a new hash from the same document a successful validation can be achieved. Considering this, the next step consists in comparing both hashes: the document will be considered valid only if both hashes are identical, according to hash properties described above. Thus, the validation of the electronic signature guarantees the document has not being tempered during its transit and is reliable.
For this reason, the implementation of signature validation systems is very important for organizations as these systems must keep compliance to European standards. The Uanataca’s Electronic Signature validation service represents a useful tool for the automated validation of signatures included on documents or transactions, offering an agile performance and an intuitive user experience.
In conclusion, the usage rate of the electronic signature over diverse business applications increases at a high speed. For this reason, is convenient to be clear about what is behind a process of signature for then understand the reasons why it represents the most adequate option in nowadays global context of great technological advances and adaptions to current situation.
In this post, although we describe the hash in a conceptual way without deeply analyzing any supporting mathematical principles has not been addressed, we have emphasized a bit more on how important hash within the electronic signature process.
It is necessary to consider the fact hash usage across the whole process is completely transparent for the end user, as his or her role will be normally limited to use a signature application for signing, receiving and/or validating documents with total guarantee of executing a fast, reliable and safe process, silently made possible by the hash algorithm.