
The number of organizations using electronic signatures on their documents gets greater every day. Its expansion has risen importance in contractual relationships. However, checking for validity of applied signatures on received documents is the same important as the implementation of an electronic signature process offering the highest legal guarantees.
In this post we’ll explain how to easily incorporate Uanataca’s electronic signature validation service in your corporate systems.
What electronic signature validation consists of?
Electronically signed documents, specially those with vital importance for the organizational activity performance, must submit to a validation process after received.
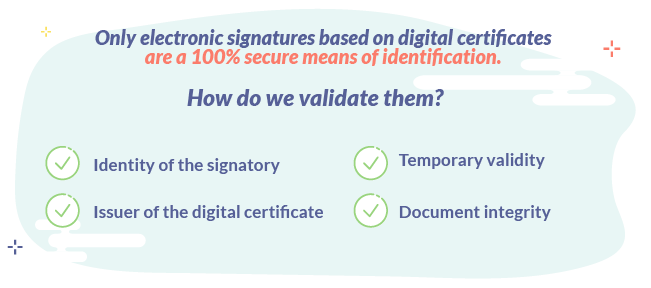
In general terms, the purpose of the signature validation is to verify the correctness of a signature applied using a digital certificate. To accomplish this, it is verified that the document has not been tampered after signature. In other words, a verification of the integrity of the document.
In the same way, the validation pursues the recognition of the signer’s identity, the electronic certificate of which is included in the signed document, and finally, to prove the validity of this certificate by requesting its corresponding issuer, the Certification Authority (CA).
Quick and easy: Just like our signature validation VOL API
Integration to Uanataca APIs is normally the kind of work that can be completed relatively fast. Particularly on our signature validation VOL API, its integration to any business application is tremendously easy, in such a way that we could summarize the process into selecting the document you want to validate, requesting for its validation, and checking the final report.
Remember an API is the English acronym of Application Programming Interface, consisting in a group of functions, known as calls or requests, that allow a client application to have access to the system backend (data accessing layer) of a third party, like Uanataca. Uanataca’s APIs are RESTful.
Uanataca, Qualified Trust Service Provider, offers all users a signature validation service in two formats. In case of single occasional validations, you can use our Web interface which represents the best option. On the other hand, when corporate needs require an adaptive solution, the integration to our API represents the ideal choice, allowing automated verification of large volumes of documents.
In this post we will cover all necessary technical aspects for including our signature validation service in your corporate systems.
VOL Optimizer: the appropriate link for safe bulk requests
As a previous step before integration, it is necessary to have a correctly installed and configured Uanataca VOL Optimizer, which must be also connected to Internet. VOL Optimizer is the name of a software that is provided as a Docker Image (for more information about Docker technology based on containers, click on the link), that receives all API requests created in a business application.
VOL Optimizer will be responsible for proving document integrity, request validation to Certification Authorities issuers of certificates that are used for signing, and finally, the reception and processing of this information to make it available for usage in the business application.
With VOL Optimizer it is possible to execute automated processes aiming to the validation of large volumes of documents in a secure way, as these documents will always remain within client premises.
How does electronically signed documents validations occur once your company receives them?
The process for signature validation via Uanataca VOL API only requires documents for validating, access credentials and our VOL Optimizer URL. As stated above, the workflow consists of a few steps:
1) Signature Validation Request
The user, from its business application, sends an API request through our VOL Optimizer. This request includes the document and his/her service access credentials.
2) Execution
Once sent the validation API request, document integrity validation starts in the Optimizer. The document representation string, known as the “hash” value of the document, is decrypted using the public key contained in the signer’s digital certificate, in turn, included in the signed document. Next, a new document hash from the original document is calculated, both are compared, and if they match, it is concluded that the document has not been tampered after signature. The same procedure applies to timestamp validation.
>> Want to know more about hash and its role in asymmetric cryptography? Check everything you need by clicking here
To determine the validity of the certificate, an OCSP (Online Certificate Status Protocol) request via Internet to issuer CA’s is triggered. Alternatively, for bulk documents Optimizer is enabled to check information from updated downloads of Certificate Revocation Lists, also known as CRL’s, provided by CA repositories. This signifies a faster and more efficient way in terms of computing processing resources.
3) Final Report
The user has the chance to choose how to obtain the result of the validation, simply by specifying in an API call a PDF report download is required, with a similar appearance to reports shown in our webpage. The other option is to adapt API retrieved JSON-format report payload in accordance to presentation requirements defined in the business application.
All the necessary to test our VOL API…close at hand!
Uanataca eases integration tasks by providing a meticulously elaborated documentation for developers including an organized presentation of every single API request with all corresponding response messages, as well as code examples in different languages that can support the developer as a first-step programming guide.
Moreover, to perform service test-oriented actions, we provide a full Postman collection with all requests available, as well as our fully-configured test VOL Optimizer with its URL ready to use!
