
Digital technologies are transforming the economy and society, causing a change in our consumption habits and in our professional relationships. The demands of the new digital client and the access to the market of a labour generation made up of digital natives, require secure communication, which guarantees a climate of stable and solid electronic transactions.
In this new digital ecosystem, guaranteeing the security of computer data and providing an accurate digital identity has become a commitment of multisectoral companies that want to ensure long-term relationships with customers and workers.
The most efficient, secure method that guarantees maximum protection against data theft is encryption, allowing only the owner and those who are authorized to manipulate it.
Electronic solutions based on the encryption method are highly dependent on the integrity and authenticity of the data, which is the reason of why great attention has to paid in security architectures, which are necessary to protect and distribute information in a wide environment.
In accordance with established paradigms, security architectures must provide four basic security services:
▪ data integrity services: they deal with the unauthorized or accidental modification of the data. This includes inserting, deleting, and modifying data. To ensure the integrity of the data, a system must be able to detect unauthorized modification of the data. The goal is for the data receiver to verify that the data has not been altered.
▪ confidentiality services: they restrict access to sensitive data only to those authorized to see it. Confidentiality measures prevent unauthorized disclosure of information to unauthorized persons or processes.
▪ identification and authentication services: they establish the validity of a transmission, a message and its source. The objective is for the receiver of the data to determine its origin.
▪ non-repudiation services: they prevent a person from denying that previous actions have been taken. The objective is to ensure that the recipient of the data is sure of the identity of the sender.
There are several technologies that can meet the aforementioned requirements, however, it is widely recognized that a comprehensive and scalable approach to security has to go through a public key infrastructure (PKI). Public key infrastructure is the combination of software, encryption technologies, and services that enables companies to protect the security of their communications and business transactions on networks.
What is a PKI?
Public key infrastructure or PKI is a combination of hardware and software, security policies and procedures.
PKI integrates digital certificates, public key cryptography, and certification authorities into a comprehensive security architecture.
A typical large-scale PKI encompasses:
▪ Generation of key pairs appropriately
▪ The issuance of digital certificates to individual users and systems
▪ End user registration software
▪ Integration with certificate directories
▪ Tools for the management, renewal and revocation of certificates, related services and support activities.
The term public key infrastructure is derived from public key cryptography, the technology behind PKI. Public key cryptography has unique characteristics that make it essential as a basis for security functions in distributed systems.
In a PKI environment, two different cryptographic keys are used for encryption and decryption purposes, known as public and private keys. The private key is kept secret by the user, and the public key can be shared and distributed. The keys are mathematically related and cannot be deduced one from each other. Data encrypted with one key can only be decrypted with the other supplemental key and vice versa. PKI encompasses a complex set of technologies. The main components are listed below:
➣ Policy and practices: they define the requirements and standards for the issuance and management of keys and certificates and the obligations of all PKI entities, and it is used to determine the level of trust offered by the certificate.
➣ Certificate Authority (CA): in an environment of PKI, a digital certificate is required, which usually contains the public key of the person, information about the certification authority and additional information about the holder of the certificate. The certificate is created and signed (electronic signature) by a trusted third party, the certification authority (CA). The identity of the individual is linked to the public key, in which the CA assumes responsibility for the authenticity of that public key, to allow a secure communication environment. The main obligations of the CA are to ensure a highly secure environment for crypto operations, as well as to issue and manage certificates.
➣ Registration Authority (RA): Provides the interface between the user and the CA. Verify the identity of the user and transmit valid requests to the CA. The registration authority (RA) is the place where it is verified that the person or organization requesting the certificate is who they say they are.
➣ PKI-enabled applications is a set of cryptographic instruments used for PKI-enabled applications, for example, communications between web servers and browsers, email, electronic data interchange (EDI), virtual private networks (VPN), etc. PKI-enabled applications typically refer to applications to which the particular CA software vendor toolkit has been added, so that they can use the vendor's CA and certificates to implement PKI functions, such as case of emails and networks to encrypt messages. The certificate policy, also called the certificate management system, is where the certification procedures are defined, including the legal responsibilities and obligations of the parties involved.
➣ Certificate distribution system: an optional component of the PKI, but which can be critical in private environments, is the certificate distribution system, which publishes the certificates in the form of an electronic directory, database or by email so that users can find them. This is usually done through a directory service. A directory server may already exist within an organization, or it may be provided as part of the PKI solution.
Overview of a PKI
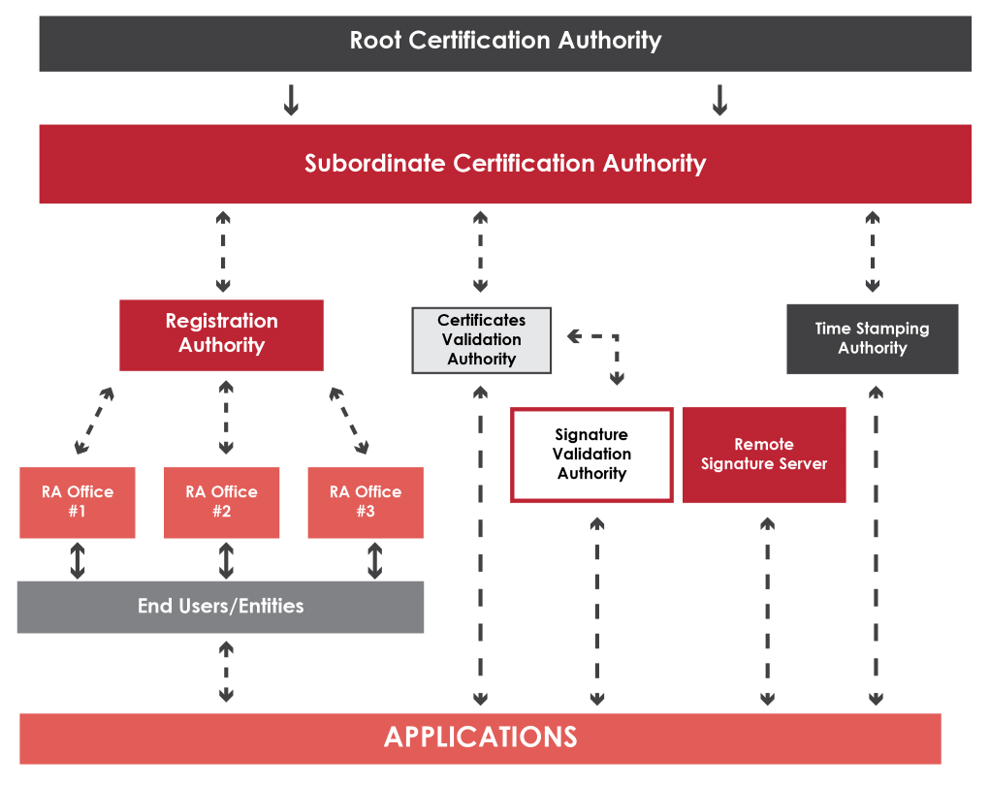
In summary, the main strengths of a PKI are:
▸ Full support for basic security services (integrity, confidentiality, identification and authentication, and non-repudiation)
▸ Global adoption and wide availability of suppliers in the market
▸ High degree of normalization in the underlying technology and operations
▸ Scalability, through various architecture models
Uanataca PKI system
A public key infrastructure (PKI) is a framework for creating a secure method of information exchange based on public key cryptography. It is widely accepted that, if applied correctly, PKI technology can provide secure and accurate identity verification, improve system security, and protect the integrity and confidentiality of information.
Uanataca offers a PKI system that meets the four fundamental requirements to establish what is called a trusted environment.
☑ Authentication
☑ Confidentiality
☑ Integrity
☑ No repudiation
Benefits of PKI technology for companies
Uanataca's PKI aaS service is the perfect solution for those companies that want to benefit from their own PKI without worries and very low investments.
The Modern PKI service from Uanataca allows you to have a PKI using Uanataca's hardware and software infrastructure, including technological services, business process consulting, procedures, human resources, legal and security. Without direct costs of technology or maintenance, taking care only of your business, you will be able to have a complete PKI with the latest technology in security, availability, performance, functionalities, services and compliance with regulations and standards.

Discover the benefits that PKI technology can bring to your business:
❂ Improve business processes, allowing time optimization, error management and cost reduction
⇩ Cost reduction, eliminating paper consumption and implementing paperless processes
⇧ Customer, worker and user satisfaction, enabling interaction at any time and from anywhere
Do you want to get the benefits of PKI technology without having your own infrastructure? With the service ☞ Modern PKI
of Uanataca you will be able to do it from the day one, without high investment. Request an offer and our expert team will contact you.